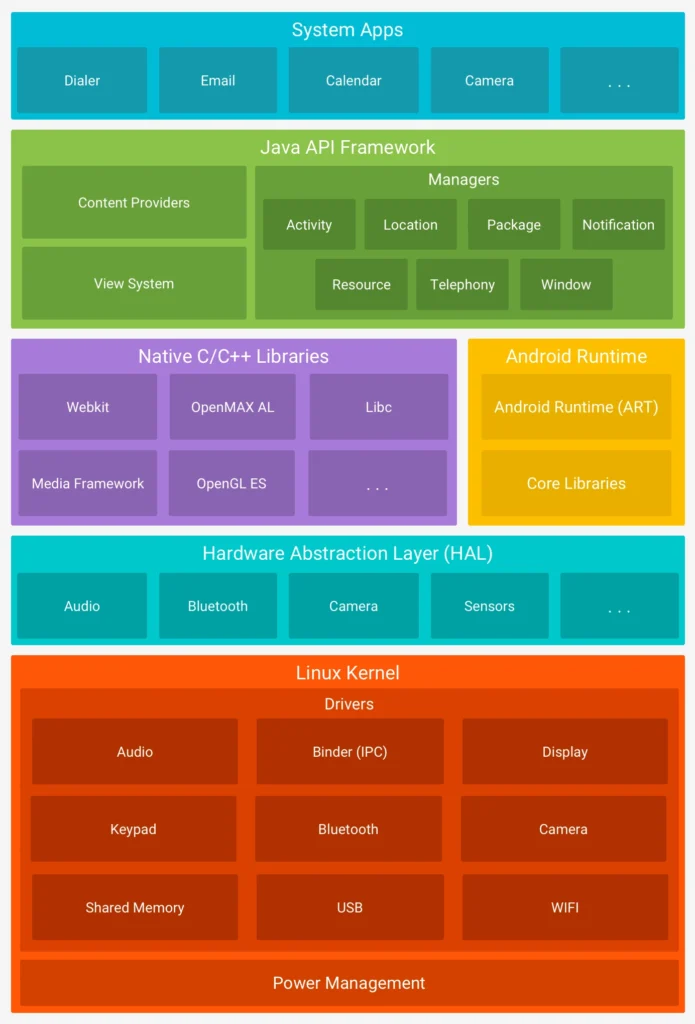
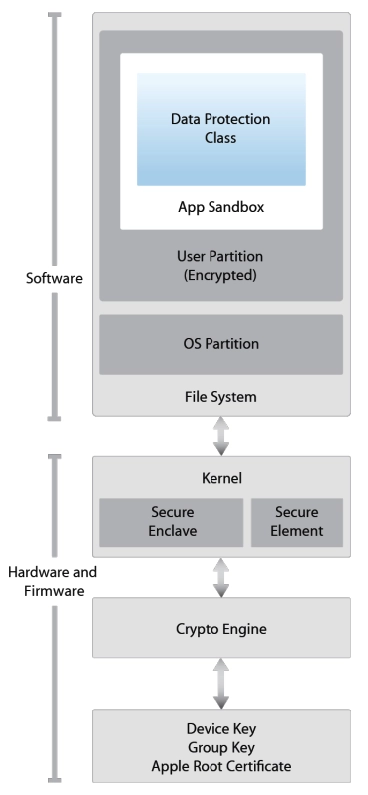
Pentesting
By Passionate CREST Certified Pentesters
CREST Certified Pentesters
Pentesters.Tech offers CREST certified Pentesting for Clients Globally.
Our CREST Certified Pentesting Team is managed by leaders who know that when it comes to Pentesting, real abilities matter. Through Pentesters.Tech, you tap directly into real world experience for real results.
Talk to us today!

Real Certified Experts:

Pentesting Services
-
 Web Application
Web Application
Pentesters -
 Black Box
Black Box
Pentesters -
 White Box
White Box
Pentesters -
 Grey Box
Grey Box
Pentesters -
 Open Box
Open Box
Pentesters -
 Closed Box
Closed Box
Pentesters -
 Internal Network
Internal Network
Pentesters -
 External Network
External Network
Pentesters -
 Red Teaming
Red Teaming
-
 Purple Teaming
Purple Teaming
-
 Android App
Android App
Pentesters -
 iOS Application
iOS Application
Pentesters -
 Active Directory
Active Directory
Pentesters -
 API Services
API Services
Pentesters -
 Desktop Application
Desktop Application
Pentesters -

Compromise Audit
-

Cyber Security
Controls Audit -

Cyber Security
Gap Assessment -

Firewall Audit
-
 GDPR
GDPR
Pentesters -
 IoT
IoT
Pentesters -
 Load / Stress Testing
Load / Stress Testing
-
MPLS
Security Audit -
Network
Resiliency Audit -

PCI DSS
Security Audit -

Secure Code Review
-
Secure Software
Development -

Social Engineering
& Phishing
Web Application Pentesting
Web applications are the most attractive targets for hackers because they are easy to reach and programmers, even when they have several years of experience often unintentionally write vulnerable, easy to exploit, code.
The goal of Web Application Pentest is to identify and repair web application security flaws.
Pentesters.Tech Web Application Pentesting team runs both manual and automated Manual Web Application Pentesters on every assignment.
Automated tools simply cannot discover all the flaws. Manual Web Application Pentesting is essential when searching for vulnerabilities, which is why out process involves 80% manual Pentesting efforts.
Conducting a Web Application Pentest protects customer loyalty and company image. Web Application Pentesting helps an organization avoid data incidents that may put the company’s reputation and reliability at stake.
Web Application Pentesting protects the integrity of assets by exposing intentionally or unintentional hidden malicious code so that code can be repaired before it is exploited. Our expert Web Application Pentesting team puts in the effort needed and investigates code line by line to expose vulnerabilities or backdoors.
Web Application Pentesting involves a methodological series of steps aimed at gathering information about the target system, finding vulnerabilities or faults in them, researching for exploits that will succeed against those faults or vulnerabilities and compromise the web application.
In our testing we include everything:
– Injections: SQL, XSS, CSRF
– Authentication tests and Session Management
– Sensitive Data Exposure checks
– Broken Access Control
– Security Misconfigurations
Our Web Application Pentesting process
Scoping – tell us what you need, or we can send you a scoping sheet for completion.
Attacking – our Web Application Pentesting Team attack your applications to discover vulnerabilities.
Reporting – We present all the weaknesses and vulnerabilities identified during the Web Application Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free.
Why our approach to Web Application Pentesting is best for you
Our Web application Pentesting service is based on PTES, NIST and OWASP standards combined with over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Web Application Pentesting sets us apart from any other Web Application Pentesting team you may come across.
Black Box Pentesting
Black Box Pentesters may also be known as:
– Single Blind Pentest
– Closed Box Penetration test
A Black Box Pentest is one where the hacker is given no background information besides the name of the target company.
A Black Box Pentest provides the Pentester with exactly the same kind of information that a Threat Actor May have. It is important during a Black Box Pentest that no one within the organisation is aware that the test is being undertaken (outside of those that arrange the test) so as to simulate real world experiences.
A Black Box Pentest can therefore be used to test the effectiveness of a Blue Team (the team charged with protecting the network).
Because of the nature of the Black Box Pentest, where a network is to be targeted, a reasonable amount of time is needed for a Black Box Pentest, think 30 plus days of activity, so as to really test what the Pentester may be able to achieve as they run through increasingly complex attack methods.
Why undertake Black Box Pentest?
– Black Box Pentesting allows for the quick identification of functional specification errors.
– Black Box Pentesting is unbiased as the architect who designed the network and the blue team that protect the network and Pentester work independently.
– Black Box Pentesting takes place using only information widely available to potential adversaries or threat actors.
– Black Box Pentesting identifies gaps in both the system and general user interfaces that may otherwise be hidden
– Black Box Pentesters simulates the behavior of a user who does not know the internal structure of the network or program, which is exactly as an external Threat Actor would experience.
Our Black Box Pentesting process
Scoping – confirm that you want the Black Box Pentest.
Attacking – our Black Box Pentesting Team undertake tasks as a Threat Actor would.
Reporting – We present all the weaknesses and vulnerabilities identified during the Black Box Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all vulnerabilities, we retest to verify for you, for Free.
Why our approach to Black Box Pentesting is best for you
Our Black Box Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Black Box Pentesting sets us apart from any other Black Box Pentesting team you may come across.
White Box Pentesting
White Box Pentesting may also be referred to as:
– Crystal Box Pentesting
– Oblique Box Pentesting
– Clear Box Pentesting
– Transparent Box Pentesting
– Open Box Pentesting
In a White Box Pentest, the Pentester is provided some information ahead of time regarding the target company’s security info.
The degree of information shared is dependent on the clients needs. In some cases the shared information may include full network and system information, including network maps and login credentials in order to test visibility to defenses.
In a White Box Pentest the aim is typically two fold, firstly to expose what the threat actor may gain access to once in the network and secondly how visible the threat actor is to defenses once they have breached the network.
In a White Box Pentest, the Blue Team (the Team Charged with protecting the network) may be advised to not stop the penetration test if observed. In other cases, the Blue Team are not warned of the White Box Pentest to determine if they could uncover a threat actor.
In a White Box Pentest the Pentester does not deliberately damage the network in any way, but rather exposes weaknesses that may be exploited by a threat actor, so these weaknesses may be remediated.
Sharing full network and system information with the tester, including network maps and login credentials helps to save time and reduce the overall cost of an engagement.
When to undertake a White Box Pentest
Many organisations choose to undertake a White Box Pentest annually, or on another predefined schedule.
Mobile Application and Web Application White Box Pentesting is normally undertaken during development, before releasing the finished product. White Box Pentesting at this stage allows weaknesses and vulnerabilities to be fixed before release.
Software and Web Application changes are a common reason for instigating a White Box Pentest. If your organisation is undertaking regular White Box Pentesters Pentesters recommends our subscription model to save cost.
White Box Pentesting Considerations
One of the criticisms of a White Box Pentest is that the sharing of information with the Pentesting team results in the Pentesters not moving through the network in a way that Threat Actors would. This, however, tends to be minimal when considering closing of weaknesses and vulnerabilities, and a combination of White Box Pentesting and Black Box Pentesting can be used over time to close this gap.
The main advantage of a White Box Pentest is that it takes significantly less time than a Black Box Pentest, saving cost.
Our White Box Pentesting process
Scoping – confirm that you want the White Box Pentest. A scoping sheet can be provided for relevant information sharing.
Attacking – our White Box Pentesting Team undertake tasks as a threat actor would.
Reporting – We present all the weaknesses and vulnerabilities identified during the White Box Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free.
Why our approach to White Box Pentesting is best for you
Our White Box Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to White Box Pentesting sets us apart from any other White Box Pentesting team you may come across.
Grey Box Pentesting
Grey Box Pentesting falls somewhere between White Box Pentesting and Black Box Pentesters.
In a Grey Box Pentest, the pentester is provided some of the access and knowledge that a user has, including, depending on scope, elevated privileges, but not full access. In some cases the organisation will also share with the Grey Box Pentester some knowledge of the network’s internals, which may include design and architecture documentation.
Grey Box Pentesting is faster than Black Box Pentesting. With access to design and architecture information, as well as in some cases having network access, pentesters can better focus their efforts and provide more in-depth analysis. This is particularly true in comparison to a Black Box Penetration test, where a pentester may never find a weakness or vulnerability that provides them access to the network.
Why undertake a Grey Box Pentest?
A Grey Box Pentest has many of the advantages of a Black Box Penetration test, without the cost. A Grey Box Penetration test is intended to be a more focused and efficient assessment of a network’s security than a Black Box Pentest.
Time is saved as Pentesters have an understanding of design and architecture and some network access, meaning they don’t have to spend time discovering this information. Having internal access also means that the Pentesters do not have to breach the hardened perimeter and can simulate an attacker who has gained access to the network.
Grey Box Pentesting process
Scoping – confirm that you want the Grey Box Pentest. A scoping sheet can be provided for relevant information sharing.
Attacking – our Grey Box Pentesters Team undertake tasks as a threat actor would.
Reporting – We present all the weaknesses and vulnerabilities identified during the Grey Box Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free.
Why our approach to Grey Box Pentesting is best for you
Our Grey Box Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Grey Box Pentesting sets us apart from any other Grey Box Pentesting team you may come across.
Open Box Pentesting
Open Box Pentesting may also be referred to as:
– Crystal Box Pentesting
– Oblique Box Pentesting
– Clear Box Pentesting
– Transparent Box Pentesting
– White Box Pentesting
In a Open Box Pentest, the Pentester is provided some information ahead of time regarding the target company’s security info.
The degree of information shared is dependent on the clients needs. In some cases the shared information may include full network and system information, including network maps and login credentials in order to test visibility to defenses.
In a Open Box Pentest the aim is typically two fold, firstly to expose what the threat actor may gain access to once in the network and secondly how visible the threat actor is to defenses once they have breached the network.
In a Open Box Pentest, the Blue Team (the Team Charged with protecting the network) may be advised to not stop the penetration test if observed. In other cases, the Blue Team are not warned of the Open Box Pentest to determine if they could uncover a threat actor.
In a Open Box Pentest the Pentester does not deliberately damage the network in any way, but rather exposes weaknesses that may be exploited by a threat actor, so these weaknesses may be remediated.
Sharing full network and system information with the tester, including network maps and login credentials helps to save time and reduce the overall cost of an engagement.
When to undertake a Open Box Pentest
Many organisations choose to undertake a Open Box Pentest annually, or on another predefined schedule.
Mobile Application and Web Application Open Box Pentesting is normally undertaken during development, before releasing the finished product. Open Box Pentesting at this stage allows weaknesses and vulnerabilities to be fixed before release.
Software and Web Application changes are a common reason for instigating an Open Box Pentest. If your organisation is undertaking regular Open Box Pentesting, Pentesters.Tech recommends our subscription model to save cost.
Open Box Pentesting Considerations
One of the criticisms of an Open Box Pentest is that the sharing of information with the Pentesting team results in the Pentesters not moving through the network in a way that Threat Actors would. This, however, tends to be minimal when considering closing of weaknesses and vulnerabilities, and a combination of Open Box Pentesting and Black Box Pentesting can be used over time to close this gap.
The main advantage of a Open Box Pentest is that it takes significantly less time than a Black Box Pentest, saving cost.
Our Open Box Pentesting process
Scoping – confirm that you want the Open Box Pentest. A scoping sheet can be provided for relevant information sharing.
Attacking – our Open Box Pentesting Team undertake tasks as a threat actor would.
Reporting – We present all the weaknesses and vulnerabilities identified during the Open Box Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free.
Why our approach to Open Box Pentesting is best for you
Our Open Box Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Open Box Pentesting sets us apart from any other Open Box Pentesting team you may come across.
Closed Box Pentesting
Closed Box Pentesters may also be known as:
– Single Blind Pentest
– Black Box Pentest
A Close Box Pentest is one where the hacker is given no background information besides the name of the target company.
A Closed Box Pentest provides the Pentester with exactly the same kind of information that a Threat Actor May have. It is important during a Closed Box Pentest that no one within the organisation is aware that the test is being undertaken (outside of those that arrange the test) so as to simulate real world experiences.
A Closed Box Pentest can therefore be used to test the effectiveness of a Blue Team (the team charged with protecting the network).
Because of the nature of the Closed Box Pentest, where a network is to be targeted, a reasonable amount of time is needed for a Closed Box Pentest, think 30 plus days of activity, so as to really test what the Pentester may be able to achieve as they run through increasingly complex attack methods.
Why undertake Closed Box Pentest?
– Closed Box Pentesting allows for the quick identification of functional specification errors.
– Closed Box Pentesting is unbiased as the architect who designed the network and the blue team that protect the network and Pentester work independently.
– Closed Box Pentesting takes place using only information widely available to potential adversaries or threat actors.
– Closed Box Pentesting identifies gaps in both the system and general user interfaces that may otherwise be hidden
– Closed Box Pentesters simulates the behavior of a user who does not know the internal structure of the network or program, which is exactly as an external Threat Actor would experience.
Our Closed Box Pentesting process
Scoping – confirm that you want the Closed Box Pentest.
Attacking – our Closed Box Pentesting Team undertake tasks as a Threat Actor would.
Reporting – We present all the weaknesses and vulnerabilities identified during the Closed Box Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all vulnerabilities, we retest to verify for you, for Free.
Why our approach to Closed Box Pentesting is best for you
Our Closed Box Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Closed Box Pentesting sets us apart from any other Closed Box Pentesting team you may come across.
Internal Network Pentesting
In an Internal Network Pentest, the ethical hacker performs the test from within the company’s internal network.
Internal Network Pentesting works from the premise that the Cyber Threat Actor already has access to your network.
This kind of test is useful in determining how much damage a disgruntled employee, ex-employee with legacy access, or a Cyber Threat Actor could potentially cause from behind the company’s firewall.
An Internal Network Pentest generally takes two broad forms:
Black Box – where little or no information is provided to the Pentesters Team.
White Box – where the organisation discloses some information to the Pentesters Team.
An Internal Pentest is useful for determining what assets are at risk and how they may be compromised. Areas of weakness can then be patched before a real-world Cyber Threat Actor finds this weakness and exploits it.
A key requirement for an Internal Network Pentest is to relax security measures to allow the Pentesters Team some latitude in finding weaknesses. Doing so, allows more weaknesses and therefore more opportunities for patching and countermeasures to be put in place, thereby improving security against real world Cyber Threat Actors.
Our Internal Network Pentesting process
Scoping – confirm that you want the Internal Network Pentest. A scoping sheet can be provided for relevant information sharing.
Attacking – our Internal Network Pentesters team undertake tasks as a Threat Actor would.
Reporting – We present all the weaknesses and vulnerabilities identified during the Internal Network Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free.
Why our approach to Internal Network Pentesting is best for you
Our Internal Network Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Internal Network Pentesting sets us apart from any other Internal Network Pentesting team you may come across.
External Network Pentesting
An External Network Pentest researches and attempts to exploit vulnerabilities that could be used by an external Cyber Threat Actor to gain access to your organisations network.
The advantage of an External Network Pentest is that your organisation can test the security of your internet facing apps, websites, servers and network perimeter before a Cyber Threat Actor does.
In an External Network Pentest, the Pentesters team always begins their simulation of a Cyber Threat Attack from outside the organisation and from there seek access to internal networks and systems. The External Network Pentesters team will simulate:
– Actions that would be taken by an external Cyber Threat Actor.
– Seek vulnerabilities at the perimeter of your organisations cyber defenses.
– Attempt to exploit vulnerabilities on compromised endpoint devices.
– Seek to gain access through web applications.
– May undertake social networking and other simulated Cyber Threat Actor attacks on personnel.
Benefits of External Network Pentesting
The real benefit of an External Network Pentest is that any weaknesses and exploits found can be used to lower the risk of an external Cyber Threat Actors actions against your organisation.
Other benefits include:
Become IT Security Compliant – IT Security Compliance regulations and guidelines require an organisation to conduct security testing to identify vulnerabilities.
Know the vulnerabilities before a real-world Cyber Threat Actor attack – an External Network Pentest lowers the gap between what is known and what remains hidden from the awareness of the stakeholders.
Insight into your cyber security posture – an External Network Pentest helps reveal how secure your organization is as well as how comprehensive is your cyber security strategy is.
Discover data leaks from your company – as part of an External Network Pentest, we will report back to you the hidden information on the internet about security breaches or data leaks from your company.
Our External Network Pentesting process
Scoping – confirm that you want the External Network Pentest. A scoping sheet can be provided for relevant information sharing.
Attacking – our External Network Pentesting team undertake tasks as a Threat Actor would.
Reporting – We present all the weaknesses and vulnerabilities identified during the External Network Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free.
Why our approach to External Network Pentesting is best for you
Our External Network Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to External Network Pentesting sets us apart from any other External Network Pentesting team you may come across.
Red Teaming Pentesting
Uncover vulnerabilities in your network, web applications, physical infrastructure and employees, with the most realistic hacking exercise available, Red Teaming Pentesting.
What is Red Teaming Pentesting?
Red Teaming Pentesting, goes beyond standard Pentesting. Red Teaming provides a no limit test based upon any all activities that a Threat Actor may undertake.
The Red Team is your adversary, behaving just as you may face in the real world.
Companies undertake Read Teaming Assessments because Read Teaming offers the most realistic attack simulations against the organization and as a result provides results that provide greater insights into the effectiveness of your entire information security program.
The techniques our red team use vary from Pentesting external infrastructure, web apps to phishing attempts aimed at employees and social engineering to impersonate employees with the goal of obtaining admin access.
Red Teaming places your organization’s security team as close to a real security incident as possible, accurately testing incident response.
Benefits of Red Teaming Pentesting
Identify software and human vulnerabilities – Red Teaming tries to find and fix vulnerabilities in all areas of your organizations: applications and employees.
Offers the most realistic state of risk for your organization – Due to real life hacking scenarios on all areas of your organization
Improve Cyber Security Program – Our team will work closely with your engineers to fix the vulnerabilities and improve the information security program
Red Teaming Pentesting exercise coverage
– Use of OSINT to discover IP Ranges and FQDNs
– Survey network topology and identify active nodes.
– Identify open ports and running services.
– Identify publicly used cloud services that may contain sensitive information
– Use of intelligence services to search for sensitive information
– Identify points of entry that could be abused to access the environment
– Review web applications to identify vulnerabilities
– Identify network infrastructure components that may have vulnerabilities
– Testing of network infrastructure services (DNS, e-mail, etc)
– Gaining foothold into systems
– Testing of externally hosted web-applications
– Use of exploits
– Use of obtained privileged access to conduct unauthorized changes
– Assess the effectiveness of preventive and detective controls placed in the environment,
– Conduct social engineering attacks: Information Gathering, Obtaining Credentials, Obtaining Access
Our Red Teaming Pentesting process
Pentesters – Web Applications, Mobile, Network, WIFI, Routers, Printers etc.
Employee Testing – Phishing attacks, Social Engineering, Pretesting, Public information discovery.
Physical Access – Pentesters.Tech offers Red Teaming with or without Physical Access Testing. Physical Access Testing of Buildings, Offices, Physical Controls, Video Cameras, Access Controls adds significantly to cost depending on your location(s) and can be arranged if needed.
Reporting – We present all the weaknesses and vulnerabilities identified during the Cloud Security Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free. Physical retesting requirements may incur a charge.
Why our approach to Red Teaming Pentesting is best for you
Our Red Teaming Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Red Teaming Pentesting sets us apart from any other Red Teaming Pentesting team you may come across.
Purple Teaming Pentesting
A purple team integrates both the Blue Team Strategy of defense, and also include the risks and vulnerabilities gathered from the Red Team.
What is Purple Teaming Pentesting?
In cybersecurity, a purple team is doing both the role of the Red Team and Blue Team. The Red Team simulated the Threat Actor, and the Blue Team is the defense.
The process involves going through both of these scenarios gathering the relevant information from each.
In a Purple Teaming Pentesting exercise the Red Team and Blue Team work together in such way that the end result is more refined and provides a deeper understanding of the company’s security.
Our Purple Teaming Pentesting process
Scoping – confirm that you want a Purple Teaming Pentesting exercise and what to include in the scope.
Attacking – our Pentesting teams undertake tasks as a Threat Actor would, refer Red Teaming for more specific details.
Reporting – We present all the weaknesses and vulnerabilities identified during the Cloud Security Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free.
Why our approach to Purple Teaming Pentesting is best for you
Our Purple Teaming Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Purple Teaming Pentesting sets us apart from any other Purple Teaming Pentesting team you may come across.
Android App Pentesting
The Android application attack surface consists of all components of the application, including the supportive material necessary to release the app and to support its functioning.
– Mobile App Authentication Architectures
– Network Communication
– Data Storage on Android
– Cryptographic APIs
– Local Authentication on Android
– Network APIs
– Android Platform APIs
– Code Quality and Build Settings for Android Apps
– Tampering and Reverse Engineering on Android
– Android Anti-Reversing Defenses
Our Android App Pentesting Methodology
XCELIT’s approach to Android App Pentesting includes reviewing how the application reacts against common input attacks, server-side controls, data communication paths and client-related issues.
Static Testing
Search for sensitive information disclosures & decompile to source code
Analyzing Config files: reveals URL, Server credentials, Cryptographic keys, Hard coded passwords
Reverse Engineering: Using reversing tools, Device Binding, Impede Comprehension, Impede Dynamic Analysis and Tampering
Dynamic Testing
Attempt to inject and bypass authentication controls & review data communications functionality
Input Validation: Injection, Malicious Input acceptance, Command Injection, Buffer Overflow, File Upload, Business logic validations, Error handling/ Info Leakage, Session management, Log tampering
Server side Testing
Vulnerabilities specific to web servers: Directory Traversal, Command injection, Remote code execution, SQL injection, Sensitive file exposure, Web server misconfiguration exploitation
API/Webservices testing: authorization, IDOR, Injections and exploits, API business logic bypass like skipping payments, API misconfigurations
Identify potential for denial of service (DOS) attacks
Our Android App Pentesting process
Scoping – confirm that you want the Android App Pentest. A scoping sheet can be provided for relevant information sharing.
Attacking – our Android App Pentesting Team undertake tasks as a Threat Actor would.
Reporting – We present all the weaknesses and vulnerabilities identified during the Android App Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free.
Why our approach to Android App Pentesting is best for you
Our Android App Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Android App Pentesting sets us apart from any other Android Pentesting team you may come across.
iOS Pentesting
Securing mobile applications is more important than ever.
What to Expect in our iOS Pentesting Service
The iOS application attack surface consists of all components of the application, including the supportive material necessary to release the app and to support its functioning.
– Mobile App Authentication Architectures
– Network Communication
– Data Storage on iOS
– Cryptographic APIs
– Local Authentication on iOS
– Network APIs
– iOS Platform APIs
– Code Quality and Build Settings for iOS Apps
– Tampering and Reverse Engineering on iOS
– iOS Anti-Reversing Defences
Our Methodology for iOS Pentesting
Our approach to iOS Pentesters includes reviewing how application reacts against common input attacks, server-side controls, data communication paths and client-related issues.
Static Testing
Search for sensitive information disclosures & decompile to source code.
Analysing Config files: reveals URL, Server credentials, Cryptographic keys, Hard coded passwords.
Reverse Engineering: Using reversing tools, Device Binding, Impede Comprehension, Impede Dynamic Analysis and Tampering.
Dynamic Testing
Attempt to inject and bypass authentication controls & review data communications functionality.
Input Validation: Injection, Malicious Input acceptance, Command Injection.
Buffer Overflow, File Upload, Business logic validations, Error handling/ Info Leakage, Session management, Log tampering.
Server side Testing
Vulnerabilities specific to web servers: Directory Traversal, Command injection, Remote code execution, SQL injection, Sensitive file exposure, Web server miss configuration exploitation.
API/Webservices testing: authorization, IDOR, Injections and exploits, API business logic bypass like skipping payments, API misconfigurations.
Identify potential for denial of service (DOS) attacks.
Our IOS Application Pentesting process
Scoping – confirm that you want the IOS Application Pentest. A scoping sheet can be provided for relevant information sharing.
Attacking – our IOS Application Pentesting Team undertake tasks as a Threat Actor would.
Reporting – We present all the weaknesses and vulnerabilities identified during the IOS Application Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free.
Why our approach to IOS Application Pentesting is best for you
Our IOS Application Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to IOS Application Pentesting sets us apart from any other IOS Application Pentesting team you may come across.
Active Directory Pentesting
An Active Directory Pentest can show weaknesses and vulnerabilities that a Threat Actor may exploit. The goal of any Pentest is to identify any possible attack vector an adversary would use in order to compromise a network.
Used by more than 90% of Fortune 1000 companies, and likely 90% of all other organisations, Active Directories are logically a target for Threat Actors.
Our Active Directory Pentesters will try a number of different methods to gain access, as you would expect of a Threat Actor.
Pentesters.Tech’s Crest Certified Pentesters perform Manual Pentesting and may also deploy Automated Pentesting in some circumstances.
Our Active Directory Pentesting process
Scoping – confirm that you want the Active Directory Pentest. A scoping sheet can be provided for relevant information sharing.
Attacking – our Active Directory Pentesting Team undertake tasks as a Threat Actor would.
Reporting – We present all the weaknesses and vulnerabilities identified during the Active Directory Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free.
Why our approach to Active Directory Pentesting is best for you
Our Active Directory Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Active Directory Pentesting sets us apart from any other Active Directory Pentesting team you may come across.
API Services Pentesting
Within Businesses it is common to find Application Programming Interfaces (APIs) that connect services and transfer data between them.
APIs are used for connection to third party applications from where it can extract information providing an avenue for data movement between services and then back to the internet.
Pentesters.Tech provides API Services Pentesters / Auditing to check if the API is exposed.
If the API is exposed or hacked the results could cause a major impact on the data being transferred. API breaches may lead to exposure of sensitive data like credit cards, medical, personal data or even tracking of your location.
Our API Services Pentesting process
Scoping – confirm that you want the API Services Pentest. A scoping sheet can be provided for relevant information sharing.
Attacking – our API Services Pentesting Team undertake tasks as a Threat Actor would.
Reporting – We present all the weaknesses and vulnerabilities identified during the API Services Pentest and recommendations on how to fix the weaknesses and vulnerabilities found.
Retesting – Once you have remediated all weaknesses and vulnerabilities, we retest to verify for you, for Free.
Why our approach to API Services Pentesting is best for you
Our API Services Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to API Services Pentesting sets us apart from any other API Services Pentesting team you may come across.
Desktop Application Pentesting
Verify the security posture of your Desktop applications against real-world cyber-attacks and repair the vulnerabilities before any breach could happen.
Rich Desktop Application Pentesting
.NET, C/C++, Microsoft Silverlight, Java applets and other types of desktop applications require thorough testing in order to be secured due to their size and the complexity of their technologies.
Using both our ethical hacking and software developers experience, we will provide clients the high-risk vulnerabilities in applications and optimum solutions to secure them.
Our Methodology for Desktop Application Pentesting
Pentesters.Tech's approach to Desktop, Thick Client Assessments includes reviewing how the Desktop Application reacts against common input attacks, server-side controls, data communication paths and potential client-related issues.
Static Testing:
Search for sensitive information disclosures & decompile to source code where possible.
Analysing Config files – reveals URL, Server credentials, Cryptographic keys, Hard coded passwords
Reverse Engineering – Using reversing tools, executable file/ jar files can be decompiled which can be modified and repackaged.
Dynamic Testing:
Attempt to inject and bypass authentication controls & review data communications functionality
Input Validation – SQL Injection, Malicious Input acceptance, Command Injection, Buffer Overflow, File Upload, Business logic validations, Error handling/ Info Leakage, Session management and Log tampering.
Server-side Testing:
Identify potential for denial of service (DOS) attacks.
Vulnerabilities specific to web servers – Directory Traversal, Command injection, Remote code execution, SQL injection, Sensitive file exposure, Web server miss configuration exploitation.
API/Webservices testing – authorization, IDOR, Injections and exploits, API business logic bypass like skipping payments, API misconfigurations.
System Testing:
Review files, registry entries, memory for sensitive information.
Exfiltration of Sensitive data from memory – applications store username, tokens, passwords, encryption keys, unscripted sensitive data. Such information is important for compromising the application.
DLL High-jacking – replacing the actual DLLs with malicious file and bypass protection mechanism.
Why our approach for Desktop Application Pentesting is best for you
Our Desktop Application Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Desktop Application Pentesting sets us apart from any other Desktop Application Pentesting team you may come across.
Compromise Audit
A Compromise Audit is used to identify an ongoing or past attack incident in your business environment.
Get a complete review of your organization’s infrastructure to identify any instances of compromise, undetected backdoors, unauthorized access, and any malicious activities.
Our Compromise Audit Methodology
Endpoint & Network Inspection – Our cyber engineers will conduct a thorough inspection of targeted or vulnerable end-points present in you environment. Specifically we are seeking indicators of malicious actives, such as sensitive data unauthorised access and remote access.
Seek Indicators of Compromise – We apply our comprehensive library of indicators of compromise to evaluate network traffic, servers, workstations, laptops, and critical log data for evidence of current and past attacker activity.
Analyze evidence – Our team will perform an extensive analysis on all findings and will provide you (the client) with recommendations on how to stay safe. Our engineers will confirm initial findings to minimize false positives prior to reporting them.
Detailed Report – We provide a detailed report that summarizes the steps taken during the assessment, the major findings and their risks, and any appropriate recommendations for next steps.
Cyber Security Controls Audit
How secure is your business?
A Cyber Security Controls Audit is a complex analysis made in order to control and investigate the level of security in a company and is designed test your Cyber Security strategy for effectiveness.
A Cyber Security Controls Audit is designed to answer many questions:
– Are there gaps in the Cyber Security strategy
– Is your company compliant with the newest regulations?
– Are the new technologies used in your company safe?
– Is your sensitive data at risk?
– Are there any potential vulnerabilities?
– Are your systems correctly configured to maintain effective security?
– Is your data encryption working properly?
Cyber Security Gap Assessment
A Cyber Security GAP Assessment will make sure that your security measures are meeting all the specific requirements in the industry that you’re active in.
Some industries have specific requirements and standards, it is essential to understand the industry’s best standards and apply them in order to be secure, compliant and gain customers trust, not to mention, build resilience against Threat Actors.
Our Cyber Security Gap Assessment Methodology
We deploy a Cyber Security Gap Assessment methodology built from many years of proven experience, as well as constant vigilance and adaption of new international standards.
The Security Framework Standard
An industry-standard security framework is a benchmark of best practices that can measure and compare your security measures with the standards.
ISO/IEC-27002 standard is specific framework provides best practices for information security management, covering key security areas such as assessment, access control, physical security, and change management.
The ISO standard provides a good framework to compare your security policies and network controls.
We will help you get compliant with the international standards of security applied to you field or industry.
Evaluation of the People and Processes
Many risks related to security breaches are caused by human intervention, such as an employee clicking a phishing email without knowing it. Do you provide employee training to keep your organization aware of changing security threats? Are standard procedures and approvals required before implementing changes?
More importantly, if you encounter a problem, is there an exit procedure? How do you handle access rights for new employees and dismissals?
We help you understand exactly how people access your organization’s network and existing security control.
Data
The goal of data collection is to understand the effectiveness of your existing security procedures operating within the technical framework. In this step, your organizational controls will be compared with best practice standards (such as ISO 27002 and NIST 800-53) and related requirements. This allows you to see how your security process matches other processes that have proven successful.
To discover gaps and vulnerabilities within your organization, obtain samples of network equipment, servers, and applications. Data collection will help to fully understand your technical environment, the security measures that have been implemented, and your overall security effectiveness.
We will help you understand how processes and data are affecting your security.
Analyzing the Cyber Security Program
The last step is a detailed analysis of your safety procedures. Our engineers will correlate the findings and create your IT security profile, including strengths and weaknesses that need improvement. Armed with this information, we can make recommendations for a security plan tailored specifically for you company. A robust security plan should consider cyber risks, staffing, budget requirements, and a timetable for completing security improvements.
We will help you optimize your security measures and will recommend the best practices in order to be fully secured.
Firewall Assessment
The firewall is the first and main line of defense between the corporate network and the public.
New developments into the industry regulations require for companies to have specific configurations and apply certain standards when it comes to their network and firewalls.
A Firewall Audit will reveal potential vulnerabilities associated with risky rules in the firewall policies, also will bring insights into on how to follow industry regulations, best practices and secure policies to implement in the corporate environment.
A Firewall Audit is a point in time audit. We recommend Firewall as a Service, for ongoing management, which saves Your Sanity, Your Time and Your Money for ongoing Firewall Management needs.
Benefits of a Firewall Audit
 | Compliance Ready Industry standards into network and firewall security are complex requiring businesses to have specific configurations and rules in place. |  | Insightful Information Clients will understand their security at a much efficient and deeper level. Also, will know how to implement the best practices in the industry. |
 | Discover Vulnerabilities An audit will uncover possible vulnerabilities and risks that comes with the implemented firewall policies and rules. |  | Improve Overall Cyber Security Understanding the risks that could be exploited and implementing the security standards will dramatically improve the security. |
GDPR Pentesting
A GDPR Pentest is needed for GDPR Compliance, but equally helps companies mitigate the risks of data breaches such as insecure encryption of data, misconfigurations, and weak access management.

What is GDPR?
The General Data Protection Regulation or GDPR is a legal framework that sets guidelines for the collection and processing of personal information from individuals who live in the European Union (EU).
Any company that operates within the EU must comply with GDPR and ensure that sensitive data is well protected. Organizations are responsible for complying with Data Subjects Rights, security such as pseudonymisation, encryption, minimization or Notifying Supervisory Authorities of data breaches within 72 hours of breach discovery.
What is a GDPR Pentest?
A GDPR Pentest is a process in which our team will analyze and guide you through the regulations, with the end goal of meeting all GDPR compliance requirements to test, assess and evaluate the effectiveness of controls and processes.
It is important to also understand that a GDPR Pentest is about more than just compliance, the GDPR Pentest is an opportunity to mitigate the risks of data breaches such as insecure encryption of data, misconfigurations, and weak access management.
Our GDPR Pentesting Methodology
Identify the risks – The main focus of this step is to Scope and Assess
At this point we are analysing and identifying Personal Identifiable Information (PII) data touch points, understand PII data processing activities and consent management, assess the risk with PII data processing and access activities, establish consent, record keeping, retention policies and procedures in according to GDPR.
Solve the issues – the main focus of this step is to provide a report with all the vulnerabilities and risks that were identified in the identification phase with recommended next steps.
Stay safe – After the remediation of the issues, we can proceed with a re-test to make sure that everything is working in compliance to GDPR.
Why our approach to GDPR Pentesting is best for you
Our GDPR Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to GDPR Pentesting sets us apart from any other GDPR Pentesting team you may come across.
IoT Pentesting
Pentesters.Tech IoT Pentesters will uncover vulnerabilities in your Smart Devices and set out plans to fix them quickly.
Internet connected devices can expose entire infrastructure to external and internal cyber threats. To secure a network, it is imperative to secure IoT devices.
Our IoT Pentesting Methodology
Firmware Reverse Engineering
Reverse engineering firmware binaries
Binary exploitation
Encryption analysis
Bypass obfuscation techniques in use
Debugging binaries to gain sensitive info
Application Pentesting
Android, Cloud and Web vulnerability testing
Input Validation: SQL Injection, Malicious Input acceptance, Command Injection Buffer Overflow, File Upload, Business logic validations, Error handling/ Info Leakage, Session management, Log tampering
Data storage vulnerabilities
Server side Testing
Identify potential for denial of service (DOS) attacks
Vulnerabilities specific to web servers: Directory Traversal, Command injection, Remote code execution, SQL injection, Sensitive file exposure, Web server miss configuration exploitation
API/Webservices testing: authorization, IDOR, Injections and exploits, API business logic bypass like skipping payments, API misconfigurations
Radio communication reversing for proprietary protocols
Hardware based exploitation
Exfiltration of Sensitive data from memory: applications store username, tokens, passwords, encryption keys, unscripted sensitive data.
UART, JTAG, SWD ports exploitation
Flash memory chips to detect a possibility to dump firmware.
Logic bugs sniffing and bus tampering
External peripheral devices: headphones, antennas etc.
Why our approach to IoT Pentesting is best for you
Our IoT Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to IoT Pentesting sets us apart from any other IoT Pentesting team you may come across.
Load / Stress Testing
Realistic simulation of peak loads before go live.
We are cyber security engineers with expertise in software performance testing and we can help you identify performance issues before your customers do.
Stress Testing Service
Stress Testing can help verify the stability and reliability of a system.
Our research led approach differentiates us from common Pentesters approaches with an objective to determine a systems robustness and error handling under extremely heavy load conditions.
Our approach includes stress testing well beyond the normal expected operating point and to evaluate how a system works under extreme conditions, to ensure that a system will not crash under heavy load situations.
Under Stress Testing (also known as Endurance Testing) as per our approach, the Application Under Testing (AUT) is stressed for a short period of time to know its withstanding capacity. Our core focus is to determine the limit, at which the system or software or hardware breaks and whether the system demonstrates effective error management under extreme conditions.
Depending on the scale that we will need to run, we can create a master-slave architecture on the AWS and do the same type of tests, distributed, built on-demand, depending on the amount of traffic that we will do the simulation with.
Services that we have conducted so far, are related to Application Layer simulations (simulation normal user different actions with different thresholds of users, different times, spikes etc.) or Volumetric attacks where we simulated with a specific nr of users/visitors decided together with the client (calculating the bandwidth that we will want to achieve).
Type of tests, all of them in conjunction with different agents operating under a master:
– Slowloris attack (different methods and headers)
– HTTP POST/GET flood
– UDP flood
– SSL/TLS renegotiation technique
Focus during Stress Testing
– To accommodate such abnormal traffic spikes.
– To check whether the system works under abnormal conditions.
– Displaying appropriate error message when the system is under stress.
– System failure under extreme conditions.
– It is better to be prepared for extreme conditions by executing Stress Testing.
Goal of Stress Testing
When Stress Testing our goal is to analyse the behaviour of the system after a failure.
For stress testing to be successful, the tested system should display an appropriate error message while it is under extreme conditions.
When undertaking Stress Testing, sometimes, massive data sets are used which may get lost during Stress Testing. Our Stress Testers check parameters to ensure they don’t lose security-related data while under stress testing.
The main purpose of stress testing is to check how fast system recovers after failure.
Load Testing Vs Stress Testing
| Load Testing | Stress Testing | |||
Load Testing is designed to test the system behaviour under normal workload conditions, and it is just testing or simulating with the actual workload. Load testing does not break the system. | Stress testing is to test the system behaviour under extreme conditions and is carried out till the system failure. Stress testing tries to break the system by testing with overwhelming data or resources. |
Methodologies and Best Practices
We follow different approach’s while performing Stress testing depending on the goal(s) to be achieved as set by the client at commencement of project.
Performance Modelling and performance testing on scaled environments are very useful and provide very good analysis of potential performance issues. However, network testing to actual volumes provides the highest level of risk mitigation when verifying the capacity and performance requirements of a system.
The most reliable and risk adverse approach is to load test to the most realistic concurrent volumes.
Distributed Stress Testing
In this image the server can connect with 2 clients (Client 1 and Client 2), but it cannot send or receive a signal from Client 3 & 4.
In distributed client-server systems, testing is done across all clients from the server.
The role of server under stress testing is to distribute a set of stress tests to all stress clients and track on the status of the client. After the client contacts the server, the server adds the name of the client and starts sending data for testing.
Meanwhile, client machines send a signal or heartbeat that it is connected with the server.
If the server does not receive any signal from the client machine, it needs to be investigated further and debugged.
Application Stress Testing
During Application Stress Testing we concentrate on finding defects related to data locking and blocking, network issues and performance bottlenecks in an application.
Transactional Stress Testing
Transactional Stress Testing is focused on stress testing on one or more transactions between two or more applications. It is used for fine-tuning & optimizing the system.
Systemic Stress Testing
Systemic Stress Testing is deployed for integrated stress testing which can be tested across multiple systems running on the same server. It is used to find defects where one application data blocks another application.
Exploratory Stress Testing
Exploratory Stress Testing is a scenario used to test the system with unusual parameters or conditions that are unlikely to occur in a real scenario. Exploratory Stress Testing is used to find defects in unexpected scenarios such as:
– A large number of users logged at the same time
– If a virus scanner started in all machines simultaneously
– If Database has gone offline when it is accessed from a website
– When a large volume of data is inserted to the database simultaneously
Load Testing Networks
Where a system can support testing to actual volumes we have a performance testing service to meet your requirements.
This service also offers a comprehensive security validation by testing your system while it is experiencing peak load and while some of that load is attacking traffic.
Our Stress Testing Methodology
Our Stress Testing process follows a 6-step plan:
Planning the Stress Test – In this step we gather system data, analyse the system and define the stress test goals
Create Automation Scripts – In this step we create the Stress Test automation scripts and generate the test data for the stress scenarios.
Script Execution – In this step we run the Stress Test automation scripts and store the stress results.
Results Analysis – In this step we analyse the Stress Test results and identify bottlenecks.
Tweaking and Optimization – In this step we fine-tune the system, change configurations and optimize code with the goal of meeting desired benchmarks.
Rerun the entire cycle – In this step we run the entire cycle to determine that changes made have produced desired results. It is not unusual to have to 3 to 4 cycles of the Stress Test process to achieve the performance goals
Tools we use for Stress Testing
LoadRunner - LoadRunner from HP is a widely-used Load Testing tool. Load Test Results shaped by LoadRunner are considered as a benchmark.
Jmeter - Jmeter is an Open-Source testing tool. Jmeter is a pure Java application for stress and Performance Testing. Jmeter is intended to cover types of tests like load, functional, stress, etc. It needs JDK 5 or higher to function.
Stress Tester - Stress Tester provides extensive analysis of web application performance.
Neo load - Neo load is a popular tool available in the market to test the web and Mobile applications. Neo load can simulate thousands of users in order to evaluate the application performance under load and analyse response times. Neo load also supports Cloud-integrated-performance, load and stress testing.
Metrics for Stress Testing
Metrics help in evaluate a system’s performance and are generally studied at the end of Stress Test.
Metrics commonly deployed by HackNo for Stress Testing are:
Measuring Scalability & Performance
Pages per Second – Measures how many pages have been requested per second. –
Throughput – Basic Metric – Response data size per second.
Rounds – Number of times test scenarios have been planned versus the number of times a client has executed
Application Response
Hit time – Average time to retrieve an image or a page.
Time to the first byte – Time is taken to return the first byte of data or information.
Page Time – Time is taken to retrieve all the information in a page.
Failures
Failed Connections – Number of failed connections refused by the client (weak signal).
Failed Rounds – Number of rounds it that failed. (Rounds – Number of times test scenarios have been planned versus the number of times a client has executed).
Failed Hits – Number of failed attempts by the system (broken links or unseen images).
Summary of our Stress Testing Service
Our Stress Testing service provides a comprehensive concurrent user simulation of user and system traffic. Stress Testing can be conducted while concurrently generating threats and attacking traffic at high loads. We can scale user behaviour to enormous maximum volumes based on your requirements. This service allows us to measure the transaction response time and service availability of your end users during periods of the highest levels of traffic.
Load testing under real world loads allows us to isolate and resolve problems before your customer encounters them. Our load testing service includes all the hardware and software to generate unlimited user loads in a realistic controlled load test.
MPLS Security Audit
Your Multi-Protocol Label Switching (MPLS) Infrastructure may not be as secure as you believe, misconfigurations may leave you exposed, and a security audit can help ensure your MPLS Infrastructure is working as expected.
Multi-protocol label switching (MPLS), is an established networking technology which has powered enterprise networks for decades. Unlike other network protocols that route traffic based on source a destination address. MPLS routes traffic based on predetermined “lables”. Businesses use MPLS to connect remote branch offices that require access to data or applications that reside in the organizations data center or company headquarters.
While cloud based services are moving to SD-WAN. MPLS will continue to have a role connecting specific point-to-point locations, like large regional offices, retail facilities with point of sale systems, regional manufacturing facilities, and multiple data centers.
Pentesters can provide MPLS Security Audit’s to ensure your MPLS Infrastructure is configured correctly.
Network Resiliency Audit
A Network Resiliency Audit focuses on the current network diagram of the organization’s data center, data recovery sites, and offices. The Network Resiliency Audit is designed to help organizations better organize their network equipment and will provide advice regarding best practices.
A Network Resiliency Audit will help strengthen your network in terms of security, and maximize the use of network components, network equipment, firewalls and more.
Key Steps in a Network Resiliency Audit
1. Planning
2. Identify Entry Points
3. Identify Perimeter Devices on the network
4. Identify Weak Links in the Design & Architecture
5. Perform a detailed checking
6. Delivery of report/recommendations
PCI DSS Pentesting
PCI DSS Pentesting regularly tests the security of network infrastructure and applications for PCI Compliance.
What is a PCI DSS Pentest?
PCI DSS Pentests are regular security assessments designed to identify and help fix vulnerabilities of external or internal network and applications.
PCI requirements demand organizations perform security audits of network infrastructure and applications at least annually, in order to remain compliant.
Our PCI DSS Pentesting Methodology
PCI DSS Pentesters is designed to cover network infrastructure and applications from both outside and inside an organisation’s network.
The methodology is based on the PTES standard and OWASP (for web applications) and includes:
– Segmentation
– Host Discovery
– Service Scanning and discovery
– Scan for Vulnerabilities
– Manual and automated exploitation
– Post-exploitation & network privilege escalation
– NAS and file servers takeover
– SMB/Net-Bios exploitation
– Credentials memory dump
– Sniffing, spoofing and relaying
– DNS vulnerability exploitation and exfiltration
Why our approach to PCI DSS Pentesting is best for you
Our PCI DSS Pentesting team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to PCI DSS Pentesting sets us apart from any other PCI DSS Pentesting team you may come across.
Secure Code Review
Detect and remediate coding flaws before they become serious Cyber Security risks.
Secure Code Review is probably the single-most effective technique for identifying security flaws. When used together with automated tools and manual Pentesters, code Secure Code Review can significantly increase the cost effectiveness of any application security verification effort.
Our Secure Code Review Methodology
Our team uses multiple code review techniques
Automated Tool Based
In this approach, the secure code review is done using different open source/commercial tools. Tools are useful in analyzing large codebase. They can quickly identify potential insecure pieces of code in the codebase, which may then be analyzed by the security analyst.
Manual White Box Analysis
In this technique, a thorough code review is performed over the whole code. Logical flaws may be identified which may not be possible using automated tools, such as business logic problems and authorization problems.
Secure Code Review Checklist
– Design – Configuration – Secure Transmission – Authentication and User Management – Authorization – Data Validation – Application Output | – Session Management – Input Validation – Cryptography – Exception Handling – Auditing and Logging – General Components – Business logic |
How our Secure Code Review process works
Scoping – Establish what needs to be tested ensuring the right approach is implemented.
Code Review – Our secure code developers review your code seeking vulnerabilities.
Reporting – We will present all the findings and solutions to fix them.
Why our approach to Secure Code Review is best for you
Our Secure Code Review team has over 10 years’ experience for each certified security engineer engaged by Pentesters.Tech. Our CREST Certified Experts and methodical approach to Secure Code Review's sets us apart from any other Secure Code Review team you may come across.
Secure Software Development
Integrate Cyber Security into your software product development.
Our team of Cyber Security engineers have expertise in software product development, and can be augmented into your team to ensure Secure Software Development. Inject our real-world Ethical Hacking expertise into your project to reduce risks from real-world Threat Actors.
One Time
For clients that are interested in a
one-time collaboration
- Choose any services you need
- A Certified Engineer will perform the services
- All vulnerabilities will be offered in our vulnerability management platform and report
- Support will be offered to fix the vulnerabilities
- Retesting the vulnerabilities is offered for free
Subscription
For clients that are interested in
long term collaboration
- Choose any services you need
- A Certified Engineer will perform the services
- You will receive access to our vulnerability management platform
- Support will be offered to fix the vulnerabilities
- Free retesting
- Any service will be available for you to request as much as needed per month
- Substantial Discount will be offered
- Real-Time collaboration with the security team
Pentesters Questions
A Penetration Test may also be known as Pentesting, a Pentest, or ethical hacking, is an authorized simulated cyber-attack on a computer system or network.
Pentesters is used to evaluate the security of the system; this is not to be confused with a vulnerability assessment which evaluates if the system is susceptible to any known vulnerabilities, assigns severity levels to those vulnerabilities, and recommends remediation or mitigation, if and whenever needed.
The primary objective of a Pentest is to identify exploitable vulnerabilities before Threat Actors are able to discover and exploit them.
Pentesters reveals real-world opportunities for hackers to compromise your applications in ways that allow unauthorized access to sensitive data or even system take-overs for malicious purposes.
Pentester’s Security Pentesters services are based on a systematic approach to vulnerability detection and reporting. Our advanced methodology includes:
Scoping – Working closely with the client to identify what assets need to have a stronger security
Intelligence Gathering – We discover all the sensitive information offered by the targeted assets that can be used by a hacker to understand and execute further attacks
Active scanning and pentesting – From industry-standard approaches, cutting edge tools and manual inspections – our comprehensive methods strive to discover all classes of vulnerabilities
Reporting, Re-adjusting & Re-testing – The vulnerabilities discovered are classified by risk and reported to the client in an easy-to-understand manner. We then discuss together discuss the best remediation approach.
If you have valuable IP, Records and Data that you want to keep isolated from Threat Actors a Penetration test is a value asset in your tool kit to use to evaluate your Cyber Security Posture.
There are a number of Penetration tests that can be performed based on your needs. For example, Pentesters can undertake Penetration tests to assess your Web Applications, what harm can be done once a firewall is breached, and even what hard can be done if someone has no knowledge of your organisation.
A Pentest can be used to identify the weaknesses that may exist within your existing Cyber Security Systems, or otherwise validate your Cyber Security Systems. We have even used Pentesters to justify spend on network hardening and solution deployment.
Your day-to-day activities may allow weaknesses to have developed over time. For this reason, Pentests are highly recommended, and many standards e.g., ISO27001, call for annual Pentesters.
Uncertain? Try a once of Penetration test with Pentesters and assess for yourself. You will be surprised.
Problem solved!
Pentesters has built a Certified, Expert, Efficient and Affordable Pentesters Team.



Social Engineering & Phishing
What is Social Engineering? Social engineering is the term used for a broad range of malicious activities accomplished through human interactions. It uses psychological manipulation to trick users into making security mistakes or giving away sensitive information.
Social Engineering techniques are: Phishing, Vishing, Impersonation, Pretexting, Spear Phishing.
Unlike automated platforms, our Social Engineering & Phishing completed by our Pentesters team is undertaken by certified experts.
We Track and Report Social Engineering & Phishing Results
Request a Free Quote